Unlocking The Power Of Security Remote Access IoT: A Game-Changer For Modern Connectivity
Security remote access IoT has become a buzzword in the tech world and for good reason. As more devices connect to the internet, the need for secure ways to access them remotely grows exponentially. Imagine being able to control your smart home devices, monitor your business operations, or manage industrial equipment from anywhere in the world—all while ensuring top-notch security. That’s exactly what security remote access IoT offers. But how does it work, and why is it so important? Let’s dive in and find out.
In today’s fast-paced digital age, the Internet of Things (IoT) has transformed the way we interact with technology. From smart thermostats to industrial sensors, IoT devices are everywhere. However, with great connectivity comes great responsibility. Ensuring that these devices are secure and accessible remotely is no longer a luxury—it’s a necessity. Security remote access IoT is the solution to this growing challenge.
As we explore this topic, you’ll discover the ins and outs of security remote access IoT, including its benefits, potential risks, and best practices. Whether you’re a tech enthusiast, a business owner, or simply someone looking to enhance your digital security, this article has something for everyone. So, grab a cup of coffee, sit back, and let’s unravel the mysteries of security remote access IoT together.
What is Security Remote Access IoT?
Security remote access IoT refers to the practice of accessing IoT devices from a remote location while maintaining robust security measures. In simpler terms, it’s like having a virtual key to your digital kingdom, ensuring that only authorized users can enter. This concept has gained immense popularity due to the increasing number of IoT devices and the demand for remote work solutions.
Think about it: you’re on vacation in Bali, but you want to make sure your office HVAC system is running efficiently. With security remote access IoT, you can log in to your system, check the temperature, and adjust settings—all from the comfort of your beach chair. Sounds pretty convenient, right? But convenience alone isn’t enough. Security is the backbone of this technology, and it’s what makes it truly revolutionary.
Why Security Matters in Remote Access IoT
When it comes to IoT, security should always be your top priority. Imagine a scenario where an unauthorized user gains access to your smart home system. They could unlock your doors, turn off your security cameras, or even manipulate your appliances. Scary, isn’t it? That’s why security remote access IoT is designed to prevent such breaches and ensure that your devices remain safe and secure.
- Discover The Ages Of Kristi Noems Children A Family Portrait
- Meet The Children Of South Dakotas Governor Kristi Noem
Here are a few reasons why security is crucial in remote access IoT:
- Protects sensitive data from cyber threats
- Prevents unauthorized access to your devices
- Ensures compliance with industry regulations
- Enhances overall system reliability and performance
Key Benefits of Security Remote Access IoT
Now that we understand what security remote access IoT is and why security matters, let’s talk about the benefits. This technology offers a wide range of advantages that cater to both individuals and businesses. From cost savings to increased efficiency, the possibilities are endless. Here’s a closer look at some of the key benefits:
1. Enhanced Convenience
One of the most significant advantages of security remote access IoT is the convenience it provides. Whether you’re managing a small home network or overseeing a large-scale industrial operation, being able to access your devices remotely saves time and effort. No more rushing back to the office to fix a minor issue or driving home to check if you turned off the stove. With security remote access IoT, you can handle everything with just a few clicks.
2. Improved Security
Security remote access IoT goes beyond convenience; it also enhances the security of your devices. By implementing advanced authentication methods, encryption protocols, and access controls, you can rest assured that your IoT ecosystem is protected from potential threats. This is particularly important for businesses that handle sensitive data or operate in critical industries.
3. Cost Savings
Implementing security remote access IoT can lead to significant cost savings. For instance, businesses can reduce the need for on-site maintenance and troubleshooting, which often involves travel expenses and downtime. Additionally, by monitoring and optimizing device performance remotely, organizations can prevent costly breakdowns and extend the lifespan of their equipment.
Challenges and Risks in Security Remote Access IoT
While security remote access IoT offers numerous benefits, it’s not without its challenges and risks. As with any technology, there are potential vulnerabilities that need to be addressed. Here are some of the most common challenges and risks associated with security remote access IoT:
1. Cybersecurity Threats
Cybercriminals are constantly evolving their tactics, and IoT devices are prime targets for attacks. From malware to phishing scams, the threats are real and can have devastating consequences. To mitigate these risks, it’s essential to implement robust security measures, such as firewalls, intrusion detection systems, and regular software updates.
2. Complexity in Implementation
Setting up a secure remote access system for IoT devices can be complex, especially for organizations with large-scale deployments. It requires careful planning, thorough testing, and ongoing maintenance. Working with experienced professionals or leveraging proven solutions can help simplify the process and ensure a smooth implementation.
3. Privacy Concerns
With so many devices collecting and transmitting data, privacy concerns are a major issue in the world of IoT. Users need to be confident that their personal information is being handled responsibly and securely. Organizations must adhere to data protection regulations, such as GDPR, and implement transparent data management practices to address these concerns.
Best Practices for Security Remote Access IoT
To maximize the benefits of security remote access IoT while minimizing the risks, it’s important to follow best practices. Here are some tips to help you get started:
1. Use Strong Authentication Methods
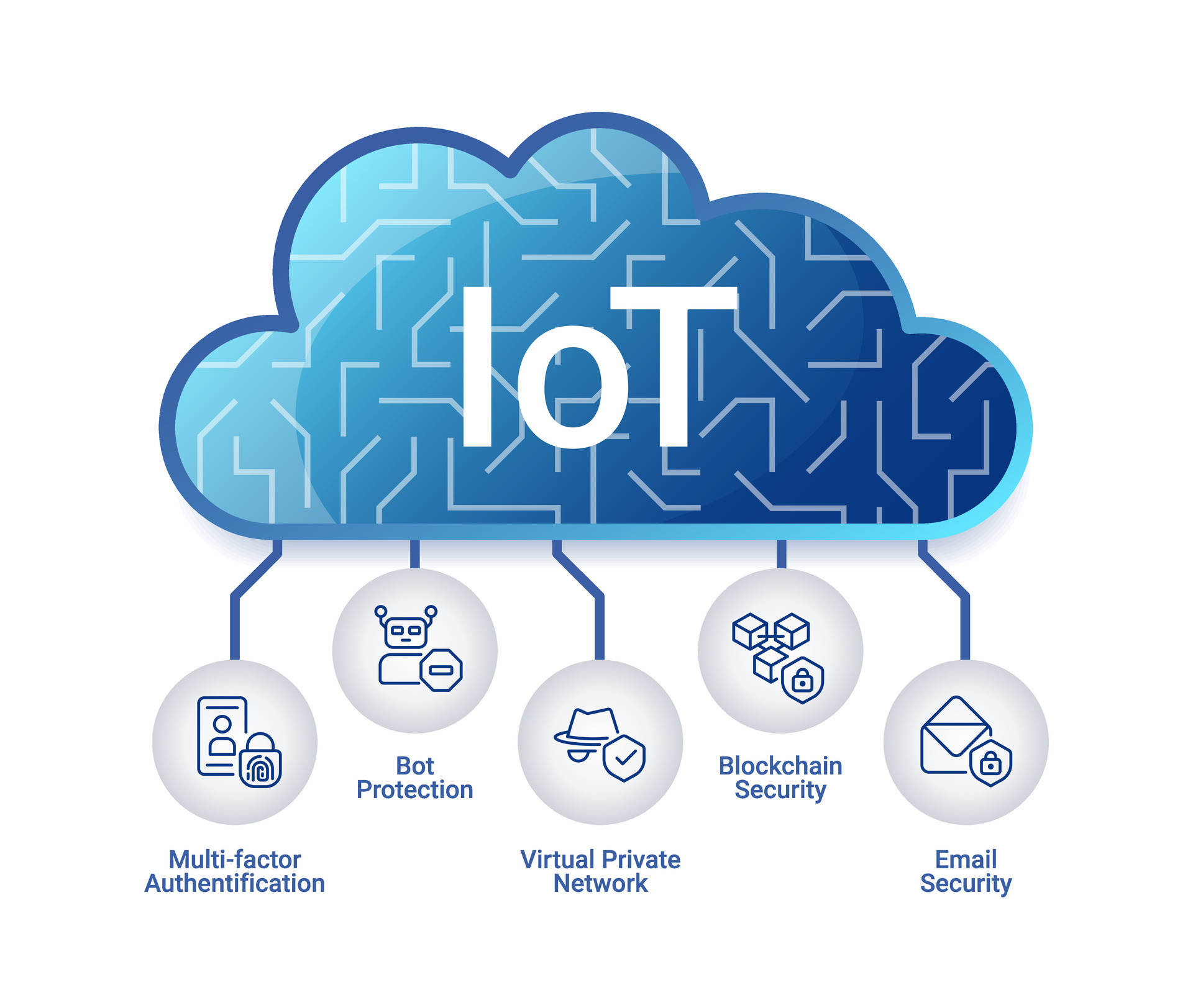
Implementing strong authentication methods, such as two-factor authentication (2FA) or multi-factor authentication (MFA), is crucial for securing remote access. These methods add an extra layer of protection by requiring users to provide additional verification beyond just a password.
2. Encrypt Data Transmission
Encrypting data transmission ensures that sensitive information is protected during transit. Use secure protocols like HTTPS, SSH, or TLS to encrypt data and prevent eavesdropping or interception by unauthorized parties.
3. Regularly Update Software and Firmware
Keeping your software and firmware up to date is essential for maintaining security. Manufacturers frequently release updates that address known vulnerabilities and improve overall performance. Make it a habit to check for updates regularly and apply them promptly.
Real-World Applications of Security Remote Access IoT
Security remote access IoT is already being used in a variety of industries, from healthcare to manufacturing. Here are a few real-world examples of how this technology is making a difference:
1. Smart Homes
Smart home systems allow users to control lighting, temperature, security, and other functions remotely. With security remote access IoT, homeowners can ensure that their systems are secure and functioning properly, even when they’re not at home.
2. Industrial Automation
In the industrial sector, security remote access IoT enables engineers and technicians to monitor and control machinery from remote locations. This capability improves operational efficiency, reduces downtime, and enhances safety.
3. Healthcare
In healthcare, security remote access IoT is used for telemedicine, remote patient monitoring, and device management. By ensuring secure access to medical devices and patient data, healthcare providers can deliver better care and improve patient outcomes.
Future Trends in Security Remote Access IoT
The future of security remote access IoT looks promising, with several emerging trends set to shape the landscape. Here are a few trends to watch out for:
1. Artificial Intelligence and Machine Learning
AI and machine learning are revolutionizing the way we approach security. These technologies can analyze vast amounts of data to detect anomalies and predict potential threats, enabling proactive security measures.
2. Edge Computing
Edge computing involves processing data closer to the source, reducing latency and improving performance. By combining edge computing with security remote access IoT, organizations can achieve faster and more secure remote access.
3. Blockchain Technology
Blockchain technology offers a decentralized and tamper-proof way to store and share data. Its application in security remote access IoT can enhance data integrity and transparency, making it an attractive option for organizations seeking advanced security solutions.
Expert Insights and Industry Statistics
To provide a more comprehensive understanding of security remote access IoT, let’s take a look at some expert insights and industry statistics:
- According to a report by Gartner, the number of IoT devices is expected to reach 25 billion by 2030.
- A study by Cybersecurity Ventures predicts that cybercrime damages will cost the world $10.5 trillion annually by 2025.
- Research from McKinsey highlights that organizations investing in IoT security can achieve up to 15% higher ROI compared to those that don’t.
Conclusion: Take Action Today
In conclusion, security remote access IoT is a game-changer for modern connectivity. It offers a wide range of benefits, from enhanced convenience and improved security to cost savings and increased efficiency. However, it’s important to be aware of the challenges and risks associated with this technology and follow best practices to ensure a secure implementation.
We encourage you to take action today by exploring the possibilities of security remote access IoT for your personal or professional needs. Don’t forget to leave a comment below and share your thoughts on this topic. If you found this article helpful, consider sharing it with your friends and colleagues. Together, let’s build a safer and more connected world!
Table of Contents
- Unlocking the Power of Security Remote Access IoT
- What is Security Remote Access IoT?
- Why Security Matters in Remote Access IoT
- Key Benefits of Security Remote Access IoT
- Challenges and Risks in Security Remote Access IoT
- Best Practices for Security Remote Access IoT
- Real-World Applications of Security Remote Access IoT
- Future Trends in Security Remote Access IoT
- Expert Insights and Industry Statistics
- Conclusion: Take Action Today


Detail Author:
- Name : Granville Herman I
- Username : padberg.martina
- Email : aaliyah.veum@vonrueden.biz
- Birthdate : 2002-12-15
- Address : 302 Carli Mall Camdenborough, ID 10038-6764
- Phone : 540-203-2798
- Company : Rowe-Green
- Job : Advertising Manager OR Promotions Manager
- Bio : Aliquam eius et aut excepturi voluptas. Nulla saepe reiciendis tempore est atque libero at. Minus ea molestiae reiciendis temporibus. Provident et nostrum recusandae dicta.
Socials
facebook:
- url : https://facebook.com/pearl4524
- username : pearl4524
- bio : Quis error ratione sunt sed soluta asperiores.
- followers : 3916
- following : 1563
tiktok:
- url : https://tiktok.com/@pearl6912
- username : pearl6912
- bio : Fugit aut quae dicta nostrum nesciunt.
- followers : 3327
- following : 2653
linkedin:
- url : https://linkedin.com/in/pearl_carroll
- username : pearl_carroll
- bio : Et a dolorem animi cupiditate quasi.
- followers : 1173
- following : 1390
twitter:
- url : https://twitter.com/pearl_carroll
- username : pearl_carroll
- bio : Sed a laboriosam ut sit. Enim hic rerum voluptas temporibus. Quidem non similique et animi facere minima earum.
- followers : 2904
- following : 1372