Unlocking The Power Of IoT SSH Tunnel AWS For Seamless Connectivity
Hey there tech enthusiasts! If you're diving into the world of IoT and looking for a secure way to connect your devices, then the concept of IoT SSH tunnel AWS might just be your golden ticket. Imagine a world where your smart devices can communicate seamlessly, securely, and efficiently. Well, buckle up because we're about to embark on a journey that will unravel the mysteries of using SSH tunnels with AWS for your IoT projects. Let's get started, shall we?
In today's hyper-connected world, the Internet of Things (IoT) is no longer a buzzword but a reality that's transforming industries. But here's the thing—security is paramount when it comes to IoT. That's where IoT SSH tunnel AWS comes into play. By leveraging SSH tunnels on AWS, you can ensure that your IoT devices are not only connected but also protected from potential threats. This setup is like giving your devices a secret handshake that only they understand.
Now, before we dive deeper, let's set the stage. This article isn't just another tech jargon-filled piece. We're going to break down the complexities of IoT SSH tunnel AWS in a way that makes sense, even if you're not a tech wizard. So, whether you're a seasoned developer or just starting out, this guide is for you. Let's make sure you walk away with actionable insights that you can apply to your projects.
What Exactly is IoT SSH Tunnel AWS?
Alright, let's cut to the chase. IoT SSH tunnel AWS is essentially a secure communication channel that allows your IoT devices to interact with AWS services without exposing them to the open internet. Think of it as a private road where only authorized vehicles can travel. This setup is crucial for maintaining the integrity and confidentiality of your data.
SSH, or Secure Shell, is a protocol that provides secure communication over unsecured networks. When combined with AWS, it becomes a powerful tool for managing IoT devices. AWS offers a robust infrastructure that supports SSH tunnels, making it easier for developers to implement secure solutions without worrying about the underlying complexities.
Here’s why IoT SSH tunnel AWS is a game-changer:
- Whos The Exhusband Of Alex Hall The Inside Scoop
- Phil Robertson Latest Breaking News And Obituary Updates
- Enhanced Security: Protects your data from unauthorized access.
- Scalability: Easily manage thousands of devices with AWS's scalable infrastructure.
- Reliability: AWS ensures that your devices are always connected, even during peak loads.
Why Choose AWS for IoT SSH Tunneling?
There are plenty of cloud platforms out there, but AWS stands out for several reasons. First off, AWS has been around for a while and has established itself as a leader in the cloud computing space. Their infrastructure is battle-tested and trusted by some of the biggest names in the industry. When it comes to IoT SSH tunneling, AWS offers a suite of services that make the process seamless.
Here are a few reasons why AWS is the go-to choice for IoT SSH tunneling:
- Comprehensive Services: AWS provides everything you need to build, deploy, and manage IoT applications.
- Global Reach: With data centers all over the world, AWS ensures low latency and high availability.
- Cost-Effective: You only pay for what you use, which makes it an attractive option for startups and small businesses.
How AWS Enhances IoT Security
Security is at the core of AWS's IoT offerings. By using IoT SSH tunnel AWS, you can take advantage of features like encryption, authentication, and access control. These features ensure that your devices are protected from potential threats. AWS also provides regular updates and patches to keep your systems secure.
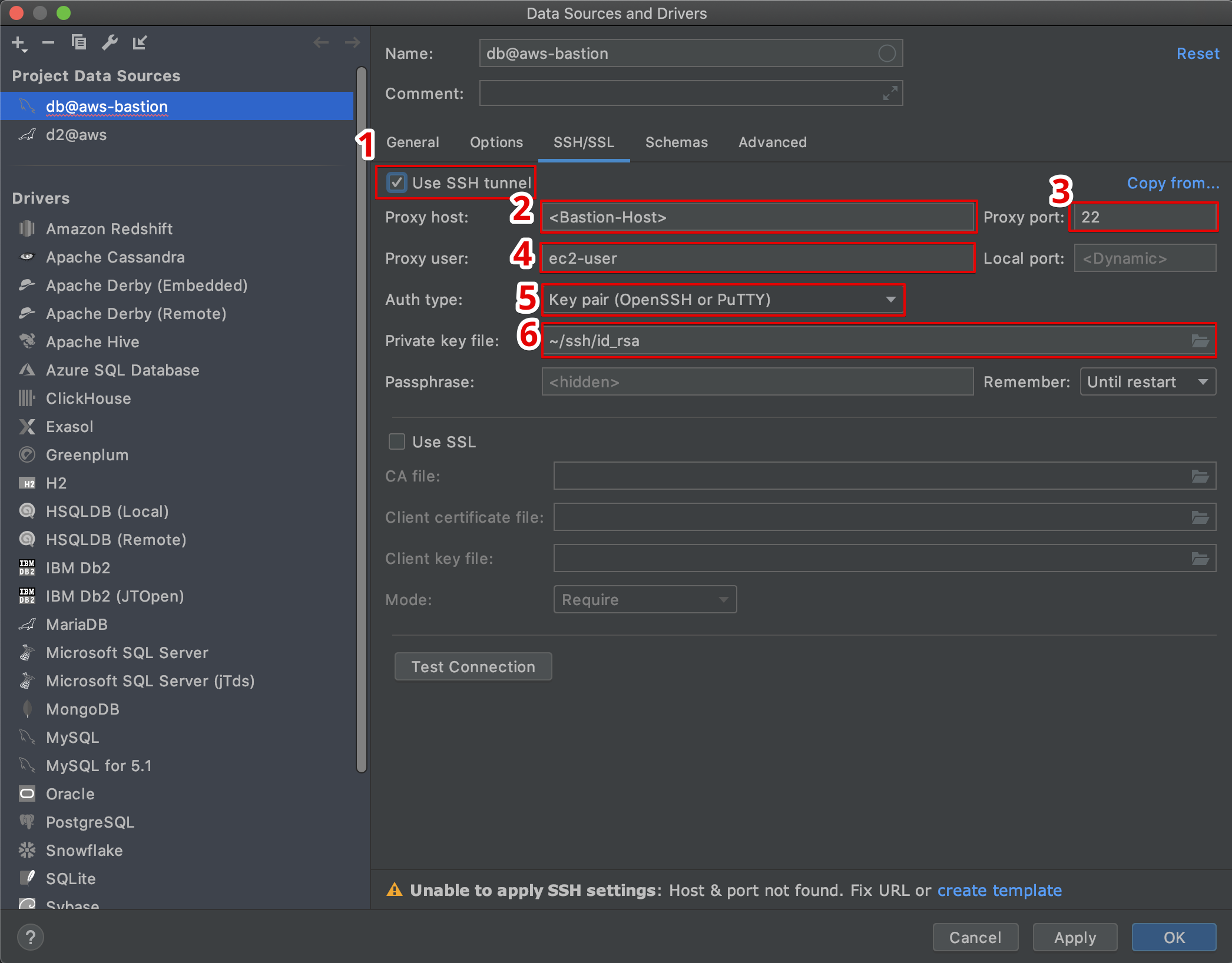
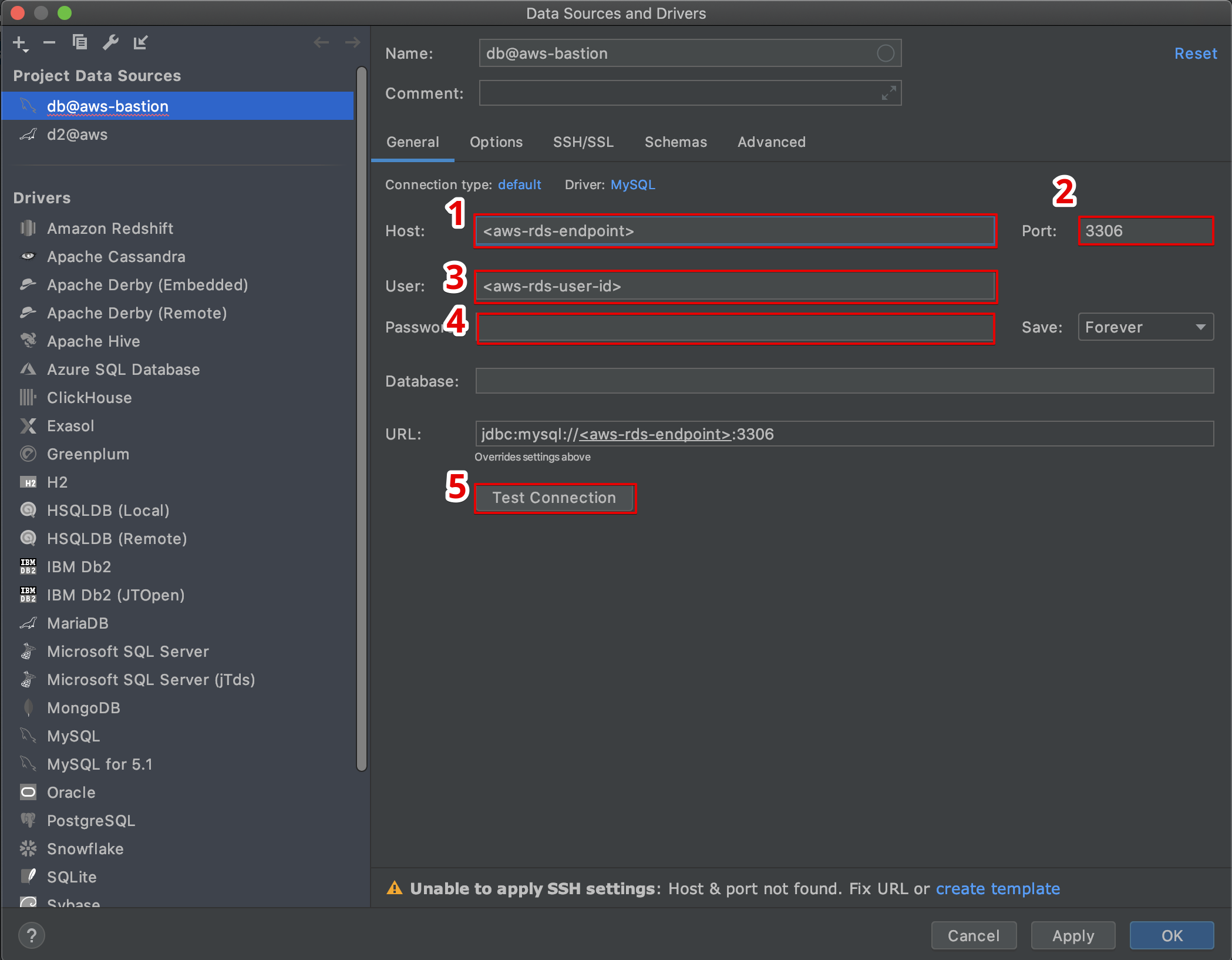
Setting Up IoT SSH Tunnel AWS
Setting up an IoT SSH tunnel on AWS might sound intimidating, but with the right guidance, it's actually quite straightforward. Let's break it down step by step:
Step 1: Create an AWS Account
If you don't already have an AWS account, you'll need to sign up for one. AWS offers a free tier that's perfect for getting started with IoT projects. Once you've created your account, you'll have access to all the tools and services you need to set up your SSH tunnel.
Step 2: Configure Your IoT Devices
The next step is to configure your IoT devices to connect to AWS. This involves setting up the necessary credentials and configurations to ensure secure communication. AWS provides detailed documentation and SDKs to help you with this process.
Step 3: Establish the SSH Tunnel
Now comes the fun part—establishing the SSH tunnel. You can use tools like SSHuttle or AWS Systems Manager to create a secure connection between your devices and AWS. This tunnel ensures that all communication is encrypted and secure.
Best Practices for IoT SSH Tunnel AWS
While setting up an IoT SSH tunnel on AWS is relatively straightforward, there are a few best practices you should keep in mind to ensure optimal performance and security:
- Regularly Update Your Devices: Keep your firmware and software up to date to protect against vulnerabilities.
- Implement Strong Authentication: Use strong passwords and multi-factor authentication to secure your devices.
- Monitor Your Network: Keep an eye on your network traffic to detect any suspicious activity.
Real-World Applications of IoT SSH Tunnel AWS
So, how exactly is IoT SSH tunnel AWS being used in the real world? Let's take a look at a few examples:
Smart Homes
Smart home devices are becoming increasingly popular, and IoT SSH tunnel AWS is playing a crucial role in ensuring their security. By using SSH tunnels, homeowners can control their devices remotely without worrying about unauthorized access.
Industrial IoT
In the industrial sector, IoT SSH tunnel AWS is used to monitor and control machinery. This setup allows companies to optimize their operations and reduce downtime by providing real-time insights into their equipment's performance.
Common Challenges and Solutions
Like any technology, IoT SSH tunnel AWS comes with its own set of challenges. Here are a few common issues and how to overcome them:
Challenge: Latency
Solution: Use AWS's global infrastructure to reduce latency and improve performance.
Challenge: Security Threats
Solution: Implement robust security measures like encryption and access control to protect your devices.
Future Trends in IoT SSH Tunnel AWS
As the IoT landscape continues to evolve, so too will the tools and technologies that support it. Here are a few trends to watch out for:
- Edge Computing: This involves processing data closer to the source, reducing latency and improving efficiency.
- AI Integration: AI will play a bigger role in IoT, enabling smarter devices that can learn and adapt to their environment.
- 5G Networks: The rollout of 5G will provide faster and more reliable connectivity for IoT devices.
Conclusion
Well, there you have it—a comprehensive guide to IoT SSH tunnel AWS. We've covered everything from the basics to advanced topics, ensuring that you have all the information you need to get started. Remember, the key to success in the IoT space is security, and IoT SSH tunnel AWS provides the tools you need to achieve that.
So, what are you waiting for? Take action today! Whether it's setting up your first IoT project or exploring new ways to enhance your existing setup, IoT SSH tunnel AWS is your gateway to a secure and connected future. Don't forget to leave a comment or share this article with your fellow tech enthusiasts. Let's keep the conversation going!
Table of Contents
- What Exactly is IoT SSH Tunnel AWS?
- Why Choose AWS for IoT SSH Tunneling?
- Setting Up IoT SSH Tunnel AWS
- Best Practices for IoT SSH Tunnel AWS
- Real-World Applications of IoT SSH Tunnel AWS
- Common Challenges and Solutions
- Future Trends in IoT SSH Tunnel AWS
- Conclusion

Detail Author:
- Name : Granville Herman I
- Username : padberg.martina
- Email : aaliyah.veum@vonrueden.biz
- Birthdate : 2002-12-15
- Address : 302 Carli Mall Camdenborough, ID 10038-6764
- Phone : 540-203-2798
- Company : Rowe-Green
- Job : Advertising Manager OR Promotions Manager
- Bio : Aliquam eius et aut excepturi voluptas. Nulla saepe reiciendis tempore est atque libero at. Minus ea molestiae reiciendis temporibus. Provident et nostrum recusandae dicta.
Socials
facebook:
- url : https://facebook.com/pearl4524
- username : pearl4524
- bio : Quis error ratione sunt sed soluta asperiores.
- followers : 3916
- following : 1563
tiktok:
- url : https://tiktok.com/@pearl6912
- username : pearl6912
- bio : Fugit aut quae dicta nostrum nesciunt.
- followers : 3327
- following : 2653
linkedin:
- url : https://linkedin.com/in/pearl_carroll
- username : pearl_carroll
- bio : Et a dolorem animi cupiditate quasi.
- followers : 1173
- following : 1390
twitter:
- url : https://twitter.com/pearl_carroll
- username : pearl_carroll
- bio : Sed a laboriosam ut sit. Enim hic rerum voluptas temporibus. Quidem non similique et animi facere minima earum.
- followers : 2904
- following : 1372