Mastering Remote Access IoT Firewall: Your Ultimate Guide To Secure Connectivity
Hey there, tech enthusiasts! Let’s dive straight into something that’s becoming more critical in today’s interconnected world. Remote access IoT firewall is not just a buzzword anymore; it’s a necessity for anyone who wants to keep their devices and data safe while accessing them from afar. As the Internet of Things (IoT) continues to expand, so does the need for robust security measures. But don’t worry, we’ve got you covered! In this article, we’ll break down everything you need to know about securing your IoT devices with firewalls, even when you’re miles away.
Now, if you’re like most people, the term "remote access IoT firewall" might sound a bit intimidating. But trust me, it’s not as complicated as it seems. Think of it as a digital bodyguard for your smart devices. Whether you’re managing a smart home, running a business, or just keeping your personal data secure, understanding how remote access firewalls work can make all the difference. So, let’s get started!
By the end of this article, you’ll have a solid grasp on what remote access IoT firewalls are, how they work, and why they’re essential for protecting your connected world. Plus, we’ll sprinkle in some actionable tips and expert advice to help you stay ahead of potential threats. Ready to level up your IoT security game? Let’s go!
- Unveiling The Truth Child And Mother Surveillance Footage Exposed
- The Versatile Performances Of Maura Tierney
Table of Contents:
- What is Remote Access IoT Firewall?
- Why is Remote Access IoT Firewall Important?
- Types of Firewalls for IoT Devices
- How Does Remote Access IoT Firewall Work?
- Benefits of Using Remote Access IoT Firewall
- Potential Challenges and Solutions
- Best Practices for Implementation
- Tools and Software for Remote Access IoT Firewalls
- Real-World Examples of Remote Access IoT Firewalls
- Future Trends in IoT Firewall Technology
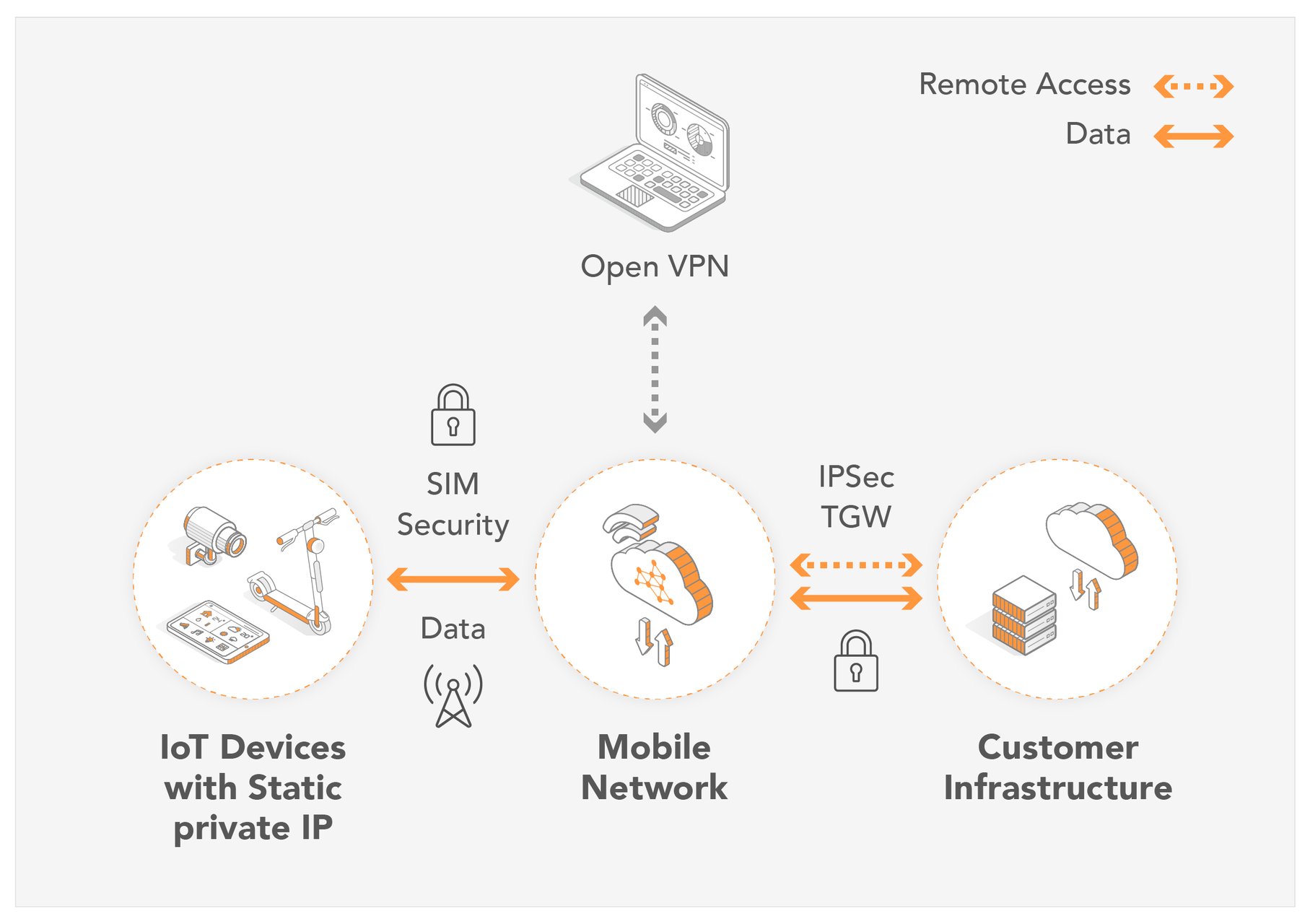
What is Remote Access IoT Firewall?
Let’s start with the basics. A remote access IoT firewall is essentially a security system designed to protect your IoT devices from unauthorized access, even when you’re accessing them from a distant location. It acts as a barrier between your smart devices and potential cyber threats, ensuring that only trusted connections are allowed.
Imagine this: you’re on vacation, but you want to check if you turned off the smart thermostat at home. With a remote access IoT firewall in place, you can do that confidently, knowing that your connection is secure and your data is protected. Cool, right?
- Watch The Unveiled Truth Kid And Mom Cctv Video Exposed
- The Tragic Fate Of Nikki Catsouras A Cautionary Tale Of Speeding And Recklessness
Now, here’s the kicker—IoT devices are notorious for being vulnerable to attacks. Without proper security measures, they can become easy targets for hackers. That’s where remote access firewalls come in, offering an extra layer of protection to keep your digital world safe.
Key Features of Remote Access IoT Firewalls
- Network segmentation to isolate IoT devices.
- Advanced threat detection and prevention.
- Encryption for secure data transmission.
- Customizable access controls for different users.
Why is Remote Access IoT Firewall Important?
Okay, so why should you care about remote access IoT firewalls? Well, let’s face it—IoT devices are everywhere. From smart refrigerators to security cameras, these gadgets are making our lives easier and more convenient. But with great convenience comes great responsibility. And that responsibility lies in keeping your devices secure.
Without a proper firewall, your IoT devices could be exposed to a wide range of threats, including malware, ransomware, and unauthorized access. These threats can compromise your personal data, disrupt your daily routines, and even cause financial losses. Yikes!
By implementing a remote access IoT firewall, you’re not only protecting your devices but also safeguarding your peace of mind. Plus, it’s a smart investment in the long run, as cyber threats are only going to become more sophisticated.
Statistics to Consider
- According to a recent study, 70% of IoT devices lack basic security features.
- Cyberattacks on IoT devices increased by 300% in the past year alone.
- Businesses lose an average of $200,000 per incident due to IoT-related breaches.
Types of Firewalls for IoT Devices
Not all firewalls are created equal. When it comes to securing IoT devices, there are several types of firewalls you can choose from, each with its own set of features and benefits. Let’s take a closer look:
1. Packet Filtering Firewalls
These are the simplest form of firewalls, filtering traffic based on predefined rules. They’re great for basic security needs but might not be enough for more complex IoT setups.
2. Stateful Inspection Firewalls
These firewalls monitor active connections and make decisions based on the state of the network. They offer better security than packet filtering firewalls but can be more resource-intensive.
3. Application-Level Gateways
Also known as proxy firewalls, these provide a high level of security by inspecting traffic at the application layer. They’re ideal for protecting sensitive IoT devices.
4. Next-Generation Firewalls (NGFW)
These are the latest and greatest in firewall technology, offering advanced features like deep packet inspection, intrusion prevention, and threat intelligence. If budget allows, NGFWs are definitely worth considering for your IoT security needs.
How Does Remote Access IoT Firewall Work?
Alright, let’s get technical for a moment. A remote access IoT firewall works by monitoring and controlling incoming and outgoing network traffic based on a set of predefined rules. It inspects each packet of data to determine whether it should be allowed or blocked.
Here’s a simplified breakdown of the process:
- Packet Inspection: The firewall examines each packet of data to ensure it meets the security criteria.
- Access Control: It checks the source and destination of the data to verify if the connection is authorized.
- Encryption: Data is encrypted to prevent eavesdropping and ensure secure transmission.
- Threat Detection: The firewall continuously scans for potential threats and blocks any suspicious activity.
By doing all of this behind the scenes, a remote access IoT firewall keeps your devices safe without you even noticing. Pretty cool, huh?
Benefits of Using Remote Access IoT Firewall
So, what exactly do you gain by using a remote access IoT firewall? Let’s break it down:
1. Enhanced Security
With a firewall in place, you can significantly reduce the risk of cyberattacks and unauthorized access to your IoT devices.
2. Peace of Mind
Knowing that your devices are secure allows you to focus on more important things, like enjoying your smart home or running your business smoothly.
3. Cost Savings
Preventing security breaches can save you a ton of money in the long run. Just think about the potential costs of data recovery, system downtime, and reputational damage.
4. Scalability
As your IoT setup grows, a remote access firewall can easily scale to accommodate more devices and connections, ensuring consistent protection across the board.
Potential Challenges and Solutions
Of course, no solution is perfect. Here are some common challenges you might face when implementing a remote access IoT firewall, along with possible solutions:
Challenge 1: Complexity
Solution: Choose user-friendly firewall software that offers intuitive interfaces and easy setup processes.
Challenge 2: Performance Impact
Solution: Opt for high-performance firewalls that won’t slow down your network or devices.
Challenge 3: Cost
Solution: Look for cost-effective solutions that provide the necessary security features without breaking the bank.
Best Practices for Implementation
Ready to set up your remote access IoT firewall? Here are some best practices to keep in mind:
- Regularly update your firewall software to ensure you have the latest security patches.
- Use strong, unique passwords for all your IoT devices and firewall accounts.
- Monitor your firewall logs to detect and respond to potential threats quickly.
- Segment your network to isolate IoT devices from other critical systems.
Tools and Software for Remote Access IoT Firewalls
There are plenty of tools and software options available for implementing remote access IoT firewalls. Some popular choices include:
1. pfSense
An open-source firewall solution that’s highly customizable and suitable for both home and business use.
2. Fortinet FortiGate
A robust enterprise-level firewall that offers advanced security features and scalability.
3. Sophos XG Firewall
A user-friendly option that provides comprehensive protection for IoT devices and networks.
Real-World Examples of Remote Access IoT Firewalls
To give you a better idea of how remote access IoT firewalls are being used in the real world, here are a few examples:
Example 1: Smart Homes
Many homeowners are using firewalls to secure their smart home devices, ensuring that their families and properties are protected from potential threats.
Example 2: Healthcare Facilities
Hospitals and clinics are implementing IoT firewalls to safeguard sensitive patient data and medical equipment.
Example 3: Manufacturing Plants
Factories are leveraging remote access firewalls to monitor and control IoT devices used in production processes, minimizing downtime and improving efficiency.
Future Trends in IoT Firewall Technology
As technology continues to evolve, so will the capabilities of IoT firewalls. Here are a few trends to watch out for:
1. AI-Powered Firewalls
Artificial intelligence is being integrated into firewalls to enhance threat detection and response capabilities.
2. Cloud-Based Solutions
More and more organizations are moving towards cloud-based firewalls for greater flexibility and scalability.
3. Zero-Trust Architecture
This approach assumes that no connection is inherently trustworthy, requiring continuous verification and authentication.
Conclusion
And there you have it, folks! A comprehensive guide to remote access IoT firewalls. By now, you should have a clear understanding of what they are, why they’re important, and how to implement them effectively. Remember, securing your IoT devices is not just about protecting your data—it’s about safeguarding your entire digital lifestyle.
So, what are you waiting for? Take action today by setting up a remote access IoT firewall and enjoy the peace of mind that comes with knowing your devices are safe. And don’t forget to share this article with your friends and colleagues who might benefit from it. Together, let’s build a safer, smarter connected world!


Detail Author:
- Name : Makayla Klein
- Username : nikki76
- Email : esta.krajcik@hotmail.com
- Birthdate : 1981-01-15
- Address : 5851 Mann Camp Suite 875 East Edythe, VA 84356-8914
- Phone : 1-646-423-8772
- Company : Wiegand-Turner
- Job : Forest Fire Fighting Supervisor
- Bio : Quod nulla quibusdam eum nostrum laborum enim et nesciunt. Aut maxime vel et nisi.
Socials
twitter:
- url : https://twitter.com/herminio_kreiger
- username : herminio_kreiger
- bio : Dicta ad aut repellendus. Numquam amet quia nihil iure. Voluptatem voluptatum reiciendis qui et nulla sed non vel.
- followers : 6554
- following : 2388
facebook:
- url : https://facebook.com/hkreiger
- username : hkreiger
- bio : Libero odit harum quia repellat repellendus ducimus.
- followers : 5978
- following : 1219
tiktok:
- url : https://tiktok.com/@herminio5500
- username : herminio5500
- bio : Exercitationem dolores ullam voluptatem autem.
- followers : 6477
- following : 2883
instagram:
- url : https://instagram.com/hkreiger
- username : hkreiger
- bio : Aliquid deleniti dolorum quia in eaque est. Blanditiis quo quasi harum ad dolore sapiente ad.
- followers : 1090
- following : 1497